BTLO - Phishing Analysis 2
Hello there everyone, I’m ninchy0. A beginner cyber defender. Hope everyone’s doing fine. Today, we will be looking at phishing analysis.
What is phishing?
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. Learn more about phishing here.
Scenario Put your phishing analysis skills to the test by triaging and collecting information about a recent phishing campaign.
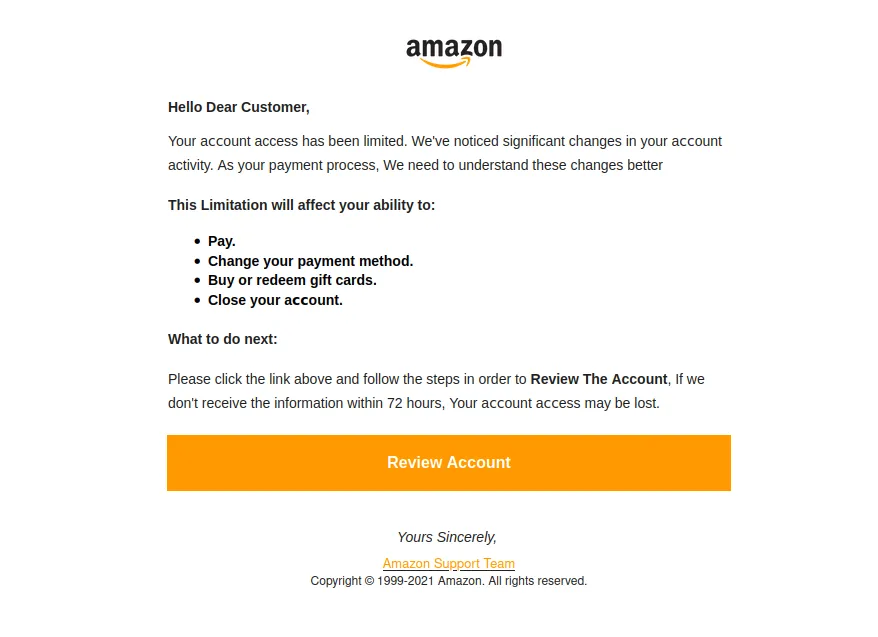
Did you check the .eml file that we got after unzipping the file? The image above is the email which we saw after opening the file. Looks legit, doesn’t it? So what is it?

Email Analysis
Every email has its sender’s email, receiver’s email, subject and more. Looking at the email via thunderbird we can see the email of the sender, subject, and email of the receiver in the top left section.
The date and time when the email was sent can be seen at the top right section.

Can you see that the attacker is faking as if the email is from Amazon?
Lets use url2png to see what the linked website looks like. Before doing that let’s understand what url2png is, URL2PNG is a fast, reliable screenshots as a Service. Cloudinary provides an add-on for using URL2PNG screenshot creation capabilities, fully integrated into Cloudinary’s image management and transformation pipeline. Learn more about it here.
So, after copying the link from the “Review Account” button and pasting in the url2png.com we can see the following.

Now, let’s copy the link from the “Review Account” button and check it from url2png. The page could not be loaded but it loaded? Hmph..
Now, let’s check the .eml file from a text editor.

The content seems to be in html which is encoded to base64.
Next, what to do?
Simple, copy and decode the base64 data and save it as something.html and open it with your browser.
After opening we can see that same email we saw in thunderbird.
Checking the source code of the html, we can see the source URL of the company’s image which looks like…

Now, let’s see where the “Amazon Support Team” link from the email takes us.

Oh Oh, Did Amazon change their support team website? XD…
Note: Always, analyze where the link in email takes us to.
Challenge Submission
1.What is the sending email address?
Ans: amazon@zyevantoby.cn
2.What is the recipient email address?
Ans: saintington73@outlook.com
3.What is the subject line of the email?
Ans: Your Account has been locked
4.What company is the attacker trying to imitate?
Ans: Amazon
5.What is the date and time the email was sent? (As copied from a text editor)
Ans: 7/13/21, 12:40
6.What is the URL of the main call-to-action button?
7.Look at the URL using URL2PNG. What is the first sentence (heading) displayed on this site? (regardless of whether you think the site is malicious or not)
Ans: This web page could not be loaded
8.When looking at the main body content in a text editor, what encoding scheme is being used?
Ans: base64
9.What is the URL used to retrieve the company’s logo in the email?
10.For some unknown reason one of the URLs contains a Facebook profile URL. What is the username (not necessarily the display name) of this account, based on the URL?
Ans: amir.boyka.7
