Embarking on 2025 and Reflecting on 2024
Very Late to the Party, But Here Are My 2024 Highlights (That No One Asked For)

Very Late to the Party, But Here Are My 2024 Highlights (That No One Asked For)

Have you ever wished you had a mischievous little sidekick to help you navigate the intricate world of hacking?
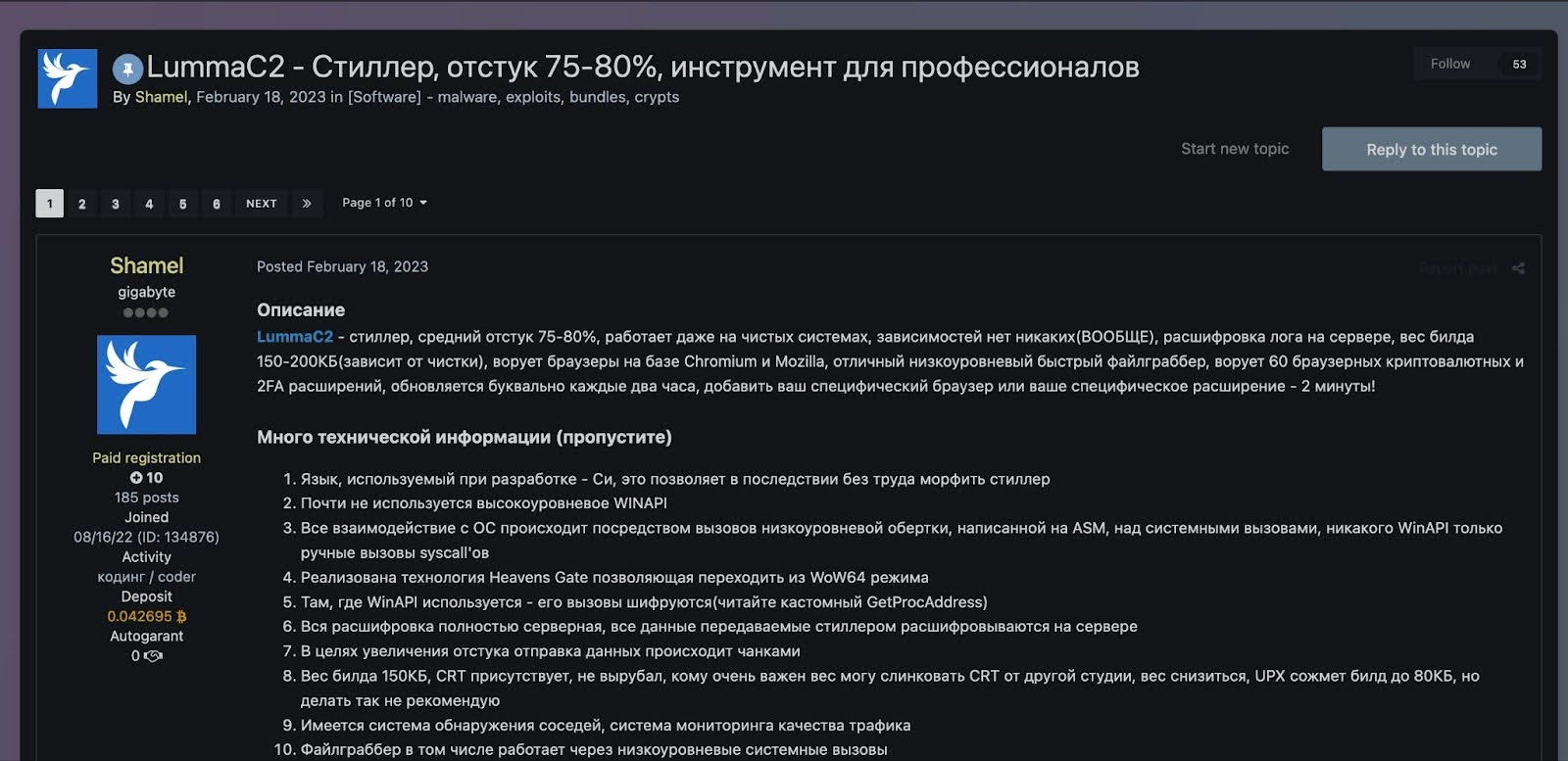
Lumma Stealer (aka LummaC2 Stealer) is an information stealer written in C language that has been available through a Malware-as-a-Service (MaaS) model on Russian-speaking forums since at least Aug...
This report covers the evolving landscape of digital and cybercrime. The report includes case study and analysis on how hacking tools was used for nationwide cyber-attack, portraying its impact. Fo...
This report is about the description of the development process of the project “Automated Incident Response for Cyber Anomalies (AIRCA)”. It is a system that automatically detects, analyses, and re...
This report covers the evolving landscape of digital and cybercrime, exploring its historical roots and the progression of malware. The report includes case studies on ALPHV BlackCat, and LockBit, ...
This report focuses on examining and addressing web injection flaws, providing demonstrations to showcase their exploitation, outlining mitigation strategies, and evaluating their advantages and di...
The report examines the incident's causes and analyses it. The breach's wider consequences, including the need for data privacy and security, are also covered, highlighting how crucial it is for pe...
This report covers modification of RSA algorithm.
The report covers various security technologies that could have potentially assisted in detecting, preventing, or even mitigating the impact of the SolarWinds attack.